Cyber Security: A definitive guide for SMEs
Contents

Part 1:
Cyber Security Basics
Before we go too far in, let's take the time to frame what Cyber Security is, and what it really means to small and medium businesses (SMEs).
What is Cyber Security?
Cyber security is the protection of computer systems (including networks and data), from theft, disruption, or manipulation.
As businesses increase reliance on computer systems, cyber security os becoming much more important and complex. The areas technology cover is always increasing; as such, this demand leads security specialists to always work on bettering the protection of IT platforms from new threats.
Some instances of technology expanding including:
- Smart devices, such as fridges, speakers, and globes;
- Internet of things (IoT), such as soil moisture sensors, connected airconditioner controllers, remote temperature sensors;
- automation, e.g. automated marketing emails, or social media chat bots; and
- machine learning (automated analysis and decision making)
- ... to name a few.
Why is Cyber Security important, especially for SMEs?
Many small business owners don’t think cyber risks are a real threat to them, and unfortunately this makes them a perfect target for cyber criminals.
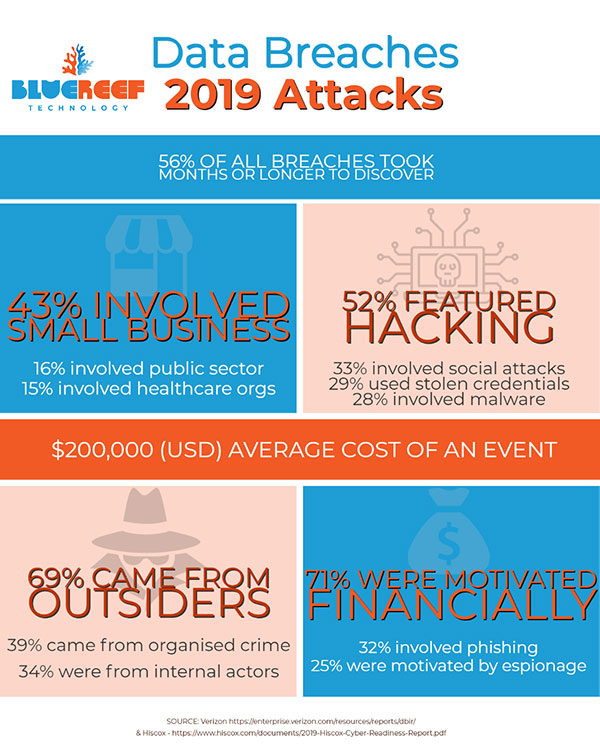
- 43% of all cyber-attacks target small businesses, according to the Australian Small Business and Family Enterprise Ombudsman, and
- 60% of those businesses who had a major event saw their business fail in the following 6 months.
What are the costs to businesses that are attacked?
The direct cost of cyber-attack to business is high.
- According to the Australian Government, this averaged $276,323 and aresolution time of 23 days (increasing to 51 days when the attack was instigated by an employee or other inside actor).
- A recent study in the US (Verizon) found the average cost of an attack on any sized business was over $200,000 USD
This length of unexpected downtime to a business' operations, as well as the direct cost of attack is unsustainable for most small businesses to endure.
What are the motivations for a cyber attack on an SME?
The major reasons for cyber attacks, as shown in a report by Verizon (2019 Data Breach Investigations Report), indicate:
- 71% are financially motivated;
- while 25% were seen to have elements of espionage.

Where can internal Cyber attacks come from?
35% of all reported data breaches in Australia from 1st April to the 31st March 2019, (via the notifiable data breaches scheme of the federal privacy act), were caused by Human error. (Interestingly - this figure rises dramatically in the health sector (55%) and financial sector (41%)).
For the most part, internal attacks are by mistake or by inadvertently assisting an external attacker gain access to internal computer systems. Some examples include:
- Human Mistakes & Error (Password mishandling, lost data storage devices (including laptops & backup media) or clicking on links that are malicious. This also often includes accidental email forwarding and similar activity);
- Social Media (Posting sensitive information into a public forum like Facebook or Reddit intentionally or by mistake);
- Malicious insiders (Espionage, data theft via cloud or USB drive, revenge);
- Inadvertent insiders (Phishing attacks, socially engineered into helping an attacker meet their goals).
Malicious insider risk also tends to increase the greater amount of authority an internal agent may have in a company (manager, or the like), specifically the greater the chance of data theft and similar activity.
What are external sources of cyber attack?
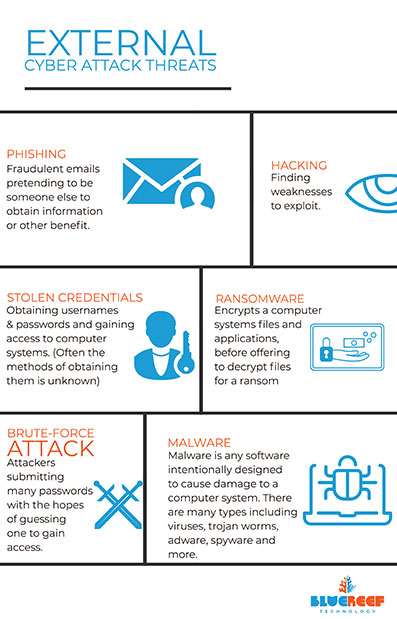
Reports out of America (Verizon) and Australia (OAIC) both have very similar results with regards to "what the bad guys are doing" when instigating data breaches:
- Phishing: fraudulent emails pretending to be someone else to obtain information or other benefit. Similar styles of attack include Spear Phishing (where emails are very targeted to a specific individual in a company like the business owner, receptionist or bookkeeper/payroll); or Whaling where high value targets and attacked only (like a CEO).
- Using Stolen Credentials: Obtaining usernames and passwords via malware or similar practice and gaining access to computer systems. (Usually the methods of obtaining them is unknown by the actual user)
- Brute-force attack: Attackers submitting many passwords with the hopes of guessing one to gain access to a computer system.
- Hacking: This can include methods liking finding and exploiting back doors, or other weaknesses in cyber security systems and gaining access to a computer system.
- Ransomware: A type of malware (Cryptovirology) which encrypts computer systems' files and applications, before offering to decrypt files for a ransom (financial gain).
- Malware: Malware is any software intentionally designed to cause damage to a computer system. There are many types including viruses, trojan worms, adware, spyware, and more.
It is important to note that there are other forms of cyber attacks, beyond security breaches.
An example is Distributed Denial of Service attacks (DDoS attack), where cyber criminals seek to make computer systems non-operational without necessarily gaining access to it. This approach usually means flooding a system with many requests to intentionally overwhelm it.

The Australian Federal Privacy Act
The Privacy Act regulates the way individuals’ personal information is handled by government organisations and businesses.
Small businesses with a turnover greater than 3 million dollars (or work in the private health sector and some other industries that handle personal information (See here if it applies to your business)) are subject to the Privacy Act.
If you qualify, you must report breaches to the office of the Australian Information Commissioner if there is unauthorised access, disclosure or loss of personal information that could compromise the persons it relates to.
For more information on this, please reach out to the OAIC. If you are unsure of your obligations still, please seek legal advice.

Part 2:
How to know if your business is at risk of Cyber Attack. (Actionable list of tasks)
Knowing there is a problem is often half the battle. The time it takes an organisation to identify and contain a breach is on average 279 days, according to a Ponemon Institute - 2019 Cost of a Data Breach Report; this also outlined that the longer a breach's lifespan is, the greater the cost.
What's worse is that 87% of small businesses believe their business is safe from cyber attack because they have antivirus alone, according to ASBFEO; which is very much not the case. This indicates there is a high rate of false confidence in their company's cyber defences.
So, it begs the obvious question... how can you be sure your business isn't at risk?
The short and painful answer is you can never be one hundred percent sure. The long answer is you can mostly be sure, provided a continued effort is in place to ensure your cyber defences are "shields up 99%".
Let's have a look at some of the methods used to find cyber security issues... (and don't worry, in the next chapter we will look at how to fix them).
Action Item #1: Security Vulnerability Assessment
You cannot beat an expert review of your business from an advisor or consultant. These are the experts who live and breathe in the technology industry and understand changing trends of technology.
Some advice you should seek from a consultant's review:
- BACKUP: Advice on the best solutions for backups for your firm - on all systems (network device configurations, Office 365, every day files);
- Cloud: Confirmation that your cloud environment (Office 365, Cloud Desktop, Website, Domain, DNS, and any other "online" assets) is reasonably secured;
- Maintenance: Is there maintenance occurring, and to what level?
- Physical: Review of your physical environment (Laptops, Servers, Firewalls, Routers, Wi-Fi, and any other physical IT equipment) is secured and protected.
- Recovery Plan: Assist in developing or refining the cyber security response plan incase there is a cyber-attack event against your firm.
- Something just for you: Identify the types of threats that may be unique to your company or industry and develop counter measures custom to you.
A decision you will also need to make early on, is the security condition level you want for your company. Basically, determine the level of cyber security you want to maintain for your company.
- Level 1 (minimal protection)
- Level 2 (advanced protection)
- Level 3 (maximum protection)
It's important to note that there are always going to be operational counter points to the level of security chosen, so you will need to find your 'Goldilocks zone'.
Higher levels of security will usually be more expensive, and take longer on a daily basis; lower will be quicker and cheaper - but less robust at defending your company.


Action Item #2: Staff, Management, and Company Culture
Company culture (and management that helps set this tone) is vitally important to a strong cyber secured company. There are some really easy ways to do this:
- Communicate safe cyber practices within the company - is the team already following them?
- Identify some ways the company could have a better security culture (training on email phishing, or similar)
- Do staff know what threats there are online?
- If a major cyber security event were to occur, how could operations continue? Are there ways you could minimise disruption?
- How would you mitigate any costs that could come from a major cyber security event (direct costs, indirect and reputation)
- Is security a road block? If so, consider ways you can get security out of the way of your team - but keep it present. Cyber Security shouldn't be a burden, but it should be top of mind.
- Are there any known likely entities that could benefit from attacking your company, and how would they benefit? Do you have a countermeasure for that?
Action Item #3: Managed, Audited environment (Logs)
With little information, little can be done. Security experts love logs, because it helps keep a record of everything that has happened in a computer system. They give clues to find breaches and close them, if they have occurred, or are currently being attempted.
The best part is, most computer systems can keep logs on almost anything, including:
- Software installations, updates or changes;
- User logins, user account changes, IP addresses they logged in from, and actions they took;
- Network activity, including what was access / changed / downloaded; and
- almost anything else that happens in a computer system.
Reviewing the logs is a lot of work, but for finding activity that shouldn't be happening, nothing beats it.


Action Item #4: Managed, audited environment (users)
Any cyber defence you may have in place becomes completely ineffective if you don't manage user accounts or access control. A good example is a staff member leaving a firm six months prior but still retaining a user account with full access. Not good!
Reviewing user accounts and making sure that only current staff/agents have access is critical to ensure a safer environment from any number of attack methods.
While doing this, it would be a really good idea to check the access logs. Has anyone been logging in using an old account? If so, you may need to implement your cyber response plan ASAP.
We'll go over users more in the next part of this guide when looking at how to further protect your business.
Action Item #5: "White Hat" hacking your own computer systems
Also known as active technical testing or penetration testing - it is the practice of ethical hackers using their skills to try and break your cyber defences.
If they can - that is actually great! You have found a vulnerability you can close so no one else can come in through the same back door.
This type of solution is good for multiple situations:
- Computers, printers, network devices, and mobiles in an office;
- In-house developed software (both publicly accessible and internally accessible);
- Server environments; and
- any other "network" connected asset.
The method of cyber attacks are constantly changing, so a solution that was secured years - or even weeks ago - may no longer be secured. Checking older systems is paramount.


Action Item #6: Business Cyber Insurance
If an unexpected cyber security event occurs, the costs of recovery can be extremely high, and cause downtime to your business anywhere from one day to months (in extreme cases, even longer).
Some of these costs associated with cyber attacks can include the following:
- Operational downtime (loss of income),
- Recovery of data,
- Getting your computer systems back into an operational state,
- Re-create any data that couldn't be recovered,
- Damage to your reputation,
- Modification to computer systems to avoid similar events,
- X-factor damage (Issues that weren't expected from a cyber attack).
Cyber Insurance can help cover these costs and help get you back online sooner.
Where possible, cyber insurance should be factored into your Cyber Security Response Plan.

Part 3:
How to protect your business from cyber threats (Action list)
Every business, no matter what computer system you use, must work to continually protect themselves from cyber attack.
The below action list are all preventative methods to protect your business from a lot of different types of cyber threats:
- Backups,
- Managed and Maintained Computer Systems,
- Passwords,
- Two-Factor Authentication,
- Safer Emails,
- Staff Training,
- User Access Control.
In the next chapter we talk about what to do if you are attacked, and many of those methods can rely on the following protection techniques to get your company back online.
Action Item #1 - BACKUP, BACKUP, BACKUP!
Backups are the most critical component of any IT recovery / cyber attack recovery plan. If you haven't had one implemented, do so as soon as possible.
Digital copies of your data should be made as frequently as possible, in a way that is as automated as possible, and to an external location. This can include two major backup solutions, as follows.
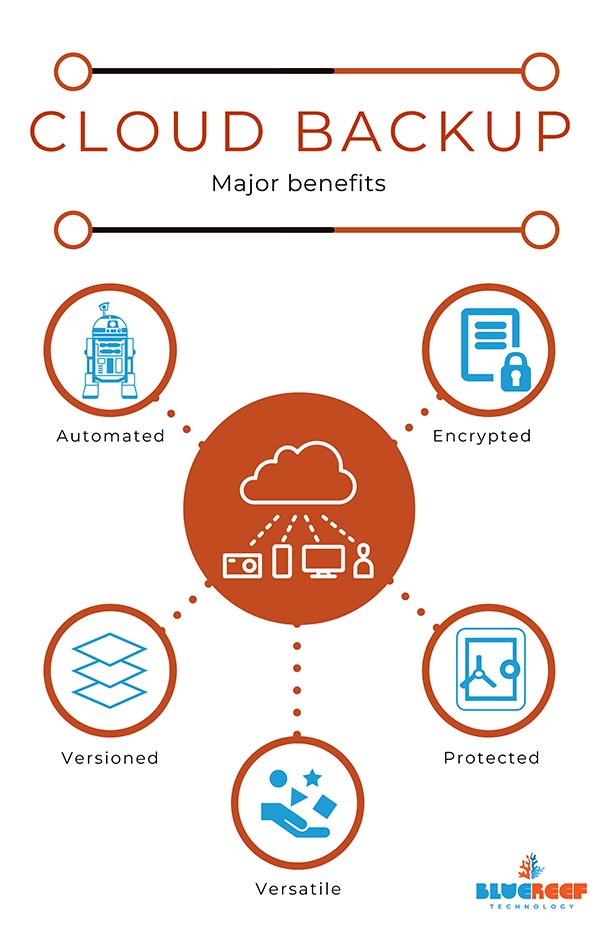
A) Cloud backup
Cloud backup is preferred as it can be set to run automatically, meaning it doesn't need human intervention to work.
Cloud backup is, by design, isolated from your computer systems and most keep versioned history of your files or other data (so you don't need to manage your backup media). They also go a step further and encrypt data more than a traditional backup generally does - this helps protect your information.
Recovering data from cloud backups can be quicker and more convenient, as it can be recovered to a completely new computer system immediately.
Depending on your IT environment, how this solution is implemented can vary.
- If you have a server, you may need to pick a solution that works specifically with databases, and full system bare metal recoveries.
- If you run multiple computers in a non-networked environment, a distributed agent style backup solution would be an ideal option for backing up your whole teams computers in a managed fashion.
- Companies that run a lot of cloud services may want to backup their cloud platforms to protect against outages of those services.
It can get more complicated the more systems that a business uses, and in those cases (and even with the above examples) we would recommend working with a Managed Service Provider (MSP) to find a solution that covers everything you need in a safe way, protecting your data.

B) Physical media (an external hard drive, tape, or USB)
With this method it is important to make sure that any drive is disconnected from the computer system when not being backed up so that it's isolated if an attack occurs (and therefore protected).
For the same reason, multiple backup medias should be used incase you need to restore back even further or the data was compromised without you knowing about it. A good number is at least 10 (one for every working except one (4), and three to keep for only once every week in rotation, and another (3) to use only once every three months in rotation).
C) Backup Best Practices
Best practices for any backup solution include:
- Scheduled regular testing of data recovery / the backup solution (try to recover said data);
- Make sure your backup solution meets regulations and/or industry guidelines (as an example, in Australia medical data cannot be stored outside of the country, therefore cloud backups from overseas providers are in breach);
- One backup solution is good, two is better; three is better still: you really cannot have enough backups, or backup methods to fall back to;
- Record confirmations of backup successes or failures - especially with automated backup solutions. (for example, email with the results of a backup session);
- Use software to manage the backup schedule, and the data that matters in the backup solution (this is especially important for physical media; cloud backups tend to do this by default).
If you don't have time to manage a backup solution (regardless of the type), you should consider outsourcing this to a Managed Service Provider (MSP) or other IT support company.
This way you have a group responsible and focused on your data backups.
D) Some things to consider when choosing an MSP:
- What level of support do you want from the solution (Business hours would be the minimum you would want here, with after-hours support if needed);
- Does this firm cover any industry regulations you have to meet (i.e. data storage in Australian only)?
- Pricing method (are they charging pay as you go, or fixed rate? Usually pay as you go works out cheaper as you don't pay for unused storage);
- Are there any other cost factors like data transfer fees or licensing fees? (most solutions don't anymore);
- Is data encrypted and physically secured in a datacentre (If not, do not proceed);
- The service providers reputation. (Do you trust them with your data?).

Action Item #2 - Passphrases, not passwords
Authentication is a major part of security in today's computer systems, and right now that means passwords - sometimes backed up with Two Factor Authentication (2FA).
All users should have passwords with a complexity that cannot be easily guessed by simple dictionary attacks or similar techniques.
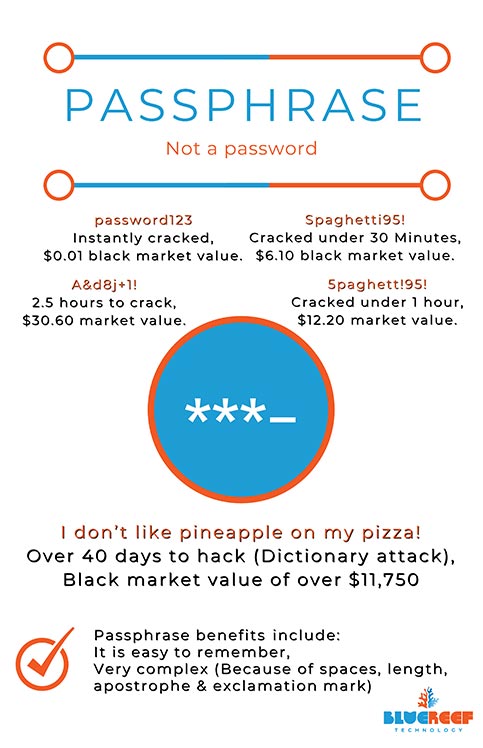
Unfortunately, even today common passwords still include for example 'Password123', 'abc123' and worst of all... 'password'. *facepalm*
To break it down:
With modern hacking tools, 'password123' can be obtained instantly, or purchased with a black market value of $0.01. Even a more complex password like 'A&d8j+1' only takes 2.5 hours to crack and can be purchased for around $30.60, according to the Australian Government Australian Signal Directorate.
Instead using passphrases is a better way to secure your accounts.
A good example of a password to use is: 'I would prefer I didn't have to use passwords!': spaces, exclamation points, and apostrophes make it easy to remember and difficult to hack; more than one year with a Brute Force attack and 40 days with a dictionary attack - a great improvement.
Action Item #3 - Employee Training and a Cyber Culture
Employees make mistakes, as all humans do. However, there are legal and ethical ramifications (not to mention financial ones) when information is stolen or systems compromised.
Staff training doesn't need to be big, or difficult; it can take multiple forms which may work better for your company culture.
Some example areas to focus on:
- How to identify a phishing email or bad email attachment.
- How to safely provide files to (and receive files from) a client or supplier.
- How to know if a website is compromised.
Training can take many forms, including:
- Online security training portals.
- Helpful hints sent to all staff fortnightly or monthly.
- One-on-one sessions with IT support staff if they are unsure of anything.
The goal is to create a cyber aware culture through the whole business to decrease the chance of events, and to spot issues before they become major incidents.


Action Item #4 - Managed, Monitored, and Maintained computer systems
To protect against malware, hacks, ransomware and more it is important to have a fully maintained computer system. This includes a few different elements:
- Updates to applications and operating systems as or as soon as possible after release.
- Updates to firmware on all devices (especially network equipment) as or as soon as possible after release.
- Vetting software before it is installed for any issues (and making sure they are integrated into the backup solution for the firm).
- Physical Firewalls and Security Gateways are updated and configuration monitored.
- Antivirus installed to all computers and updated everyday (every three hours where definitions are on that cycle).
- Software firewall or Internet filter deployed to all portable devices that may not be protected by the physical firewall of the place of business
- Identification of threats that may be operating within your computer network (like unsupported Windows Operating systems, or rouge software).
- Extended management of other IT assets (user accounts, server hardware, and more).
Once you have the above basics in place, the next priority is to monitor and maintain in an ongoing basis. This often takes the form of a managed IT service from a MSP company.
Action Item #5 - User Access Controls
Limiting access to areas of the business computer systems that staff don't need in order to do their job helps segment risk.
An example is if a receptionist computer is taken down by malware, only the files that person has access to would be compromised. Because the receptionist doesn't have access to other files - in most cases - this would also protect those files.
This also protects from other threats to business data like internal espionage and data theft.
Staff should also be warned to not share their passwords/passphrases and not keep passwords in easily obtainable locations (ie. post-it note on their desk). As staff members leave the company, their accounts should be disabled as soon as possible.
In most cases, the least privilege a user needs to complete their role is what should be granted, to achieve this protection. Access level controls be be extended onto:
- Networks
- Applications
- Files
- Data
- Services (web hosting, etc).
In all cases, Administrator privileges should not be granted to any staff except a dedicated IT person and/or their company representative.


Action Item #6 - Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is a powerful tool to enhance traditional passwords which aren't always a strong defence.
It works by requesting, in addition to a password, a code which changes continually from an app on a mobile phone (like Google Authenticator / Microsoft Authenticator), text message, or physical token. Both the password and code are required to be entered in addition at login, to grant access to a computer system.
With 2FA, even if a password is stolen or guessed, you also need the 2FA code before gaining access to the computer system in question.
2FA is available on most platforms now, and is fast becoming an industry standard across the board.
Common business applications two-factor authentication can be enabled on include Xero, MYOB, Banks, Office 365, and more.
Action Item #7 - Safer emails with Phishing filters, and Managed Antivirus
Email is a major point of entry into business systems for malware, and often socially engineered like phishing attacks on companies. Because of this, it's important to deploy additional security tools to protect email services in your domain.
Most email services (like Office 365, Google Mail, and others) have in-built tools that help with basic protection. These includes tools like whitelists, IP address filters, and usually all preconfigured. They can be altered to provide better protection, but usually the best way forward is via more advanced third party tools focusing on email security.
These types of services include:
- Email antivirus filters for mail servers. These use enterprise-grade antivirus services to scan emails coming in at the server-level, before emails are handed off to end users);
- Phishing and social threat filters for mail servers. These services determine the likelihood of an email being real more effectively than standard tools. However, even these A.I. powered solutions aren't 100% accurate (false-positives), which is why...
- Phishing Threat Training tools are really good. They can help simulate a phishing attack on your own company and identify whether you should spend more time training your staff against this type of threat.
- Email Archive / Managed Service. These server-level email archive tools are really good because they backup emails as the server receives them. If a staff member deletes the email on their own account (or it is attacked), it doesn't matter, as you have it saved in a separate archive.


Part 4:
What to do if you have been hacked?
The initial actions you take after a cyber event could determine how long your business is offline, so being clear on what is required is key.
Cyber Attack First Actions: Quick is key
The first things to do when you are hacked is:
- Let the team, and your IT partner, know what has happened - and what you have done already to help work the issue. (Your IT Partner will help guide you from here).
- Reset passwords (and turn on 2FA if you haven't already done so).
- Disconnect devices from the network, and isolate them from the Internet.
- Get your Cyber Response Incident Response Plan you have previously prepared, and action it.
Once these basic four steps have been actioned, you can focus on recovery and after-action identification.
How do you identify a source of attack?
Once you have isolated any equipment that has been affected, and reset all passwords, you will want to reach out to your IT partner. They will help you:
- Determine the source of the attack;
- Make sure that source of the attack is locked down, so it can't happen again;
- Identify if data has been obtained from the incident;
- Identify if data has been modified or encrypted from the attack;
- Confirm if any cloud accounts have been compromised (inclulding email accounts, your business website, or others);
- Overall, perform a personalised system health check to make sure there are no bad guys left with access to systems, routers, or similar.
Once the source has been identified, you can quickly move to the recovery of your business computer systems.


How to recover from a Cyber Attack
There are a number of different factors that make this a difficult question to cover. It will be largely determined by your overall computer system design, and by what your IT partner found from their initial review of your network.
- If the attack hit a single computer or device, recovery can be a single day. The device can be recovered from backups or wiped completely if required.
- If the cyber attack damages an entire network or computer system, recovery can be anywhere up to 23 days or longer depending on how much damage has been caused.
The actual method of recovery usually involves all systems being isolated, and bringing systems online one by one until the IT platform as a whole is back online.
The reason for this staggered approach is to ensure all traces of malware or 'hacker's code' is removed or plugged before moving onto the next part of recovery.
Communication with Clients, Suppliers, and the Government is key
Clients and Suppliers: Keeping in contact with your clients and suppliers is going to be key throughout this process. The purpose is twofold: first, you will need to let them know about any unforeseen delays to your deliverables (or receivables) with them.
Second, as you identify any sources of attack that may also put them at risk, you must let them know immediately (we recommend via phone call, not reply email) so their own IT teams can put measures in place.
The Australian Privacy Act: If you have found a breach that has released personal information to unauthorised persons, you need to report it to the Australian Information Commissioner.
Australian Signals Directorate: ASD is Australia's foreign signals intelligence, cyber security and offensive cyber operations agency. You can report cybercrime on their website.


Part 5:
Always be vigilant with cyber security
- Staff training, and a culture of security
- Access control limitations
- Updates of all computer systems
- Regular, ongoing maintenance
- Passphrases instead of passwords
- Two-Factor Authentication
- Backups (backups, backups!)
- A good cyber threat response plan for your business
- Managed, Audited environment
- Safer emails (spam, phishing tools)
- Cyber insurance for your business
- A strong relationship with an IT provider.
Cyber threat evolution
If you are interested, please feel free to check out BlueReef Technology's IT Services, which includes Cyber Security:





08 8922 0000